Intelligence-Driven Computer Network Defense Informed by Analysis of Adversary Campaigns and Intrusion Kill Chains.
- Traditional incident response methods are reactive, which renders them partially inefficient in many current scenarios.
- New threats such as APT (advanced persistent threat) are on the rise. They are based around undetected system infiltration which can span over years. Such attacks are usually highly sophisticated and difficult to defend against if they are not specifically expected and the target does not possess any background information of the threat actors.
- Kill chain models can improve the defense mitigate the vulnerability against such attacks by mapping potential attack structures, and reducing the risk as well as success rate of APTs.
Kill chains are systematic processes for the engagement and targeting of an objective, which originally originated in the military complex. In the world of data security the same model has served as useful base in areas such as intrusions.
Kill Chain Phases (from a computer network attack perspective)- Reconnaissance: Identify the target and gather intelligence. This includes among others digital, physical, and human resources.
- Weaponization: The preparation of a deliverable payload. This can be digital files or physical devices which will be weaponized with malicious functionality.
- Delivery: The transmission or delivery of the weaponized payload. This could be an email attachment, USB device, etc.
- Exploitation: Once the delivery is successful the payload will be triggered/executed.
- Installation: With the help of the triggered payload we ensure persistence in the target system and accessibility from the outside.
- Command and Control (C2): Compromised targets often report to a control server to establish a C2 channel.
- Action on Objectives: After all previous phases are completed we can begin with the main part of the attack. This could be data theft, encryption, sabotage, further compromise, etc.
By gaining a full understanding of the kill chain, it becomes easier to detect and test for potential paths of attack, as well as test how effective the implemented defenses are. This is easier said than done and also depends strongly on the capabilities of both the attacker and defender.
Since this process is rather resource intensive and difficult to quantify in terms of ROI, many companies ignore its importance until it is too late. We can see a reflection of that in the countless news articles where extremely sensitive data is stolen, encrypted through ransomware, and so on. These cases span from power plants, voting systems, defense manufacturers, to insurances, and so on.
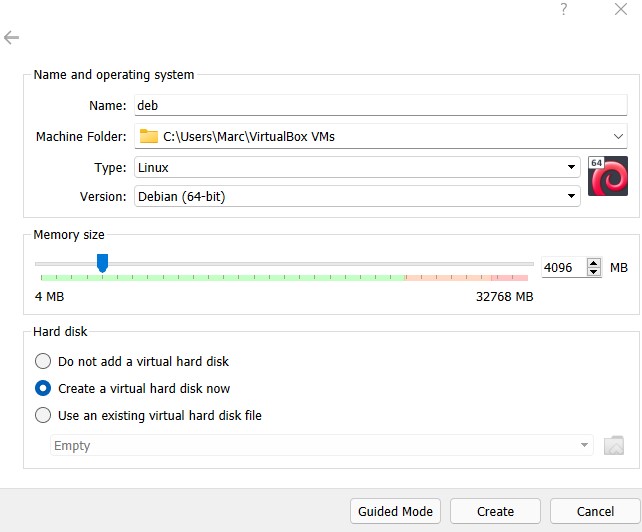
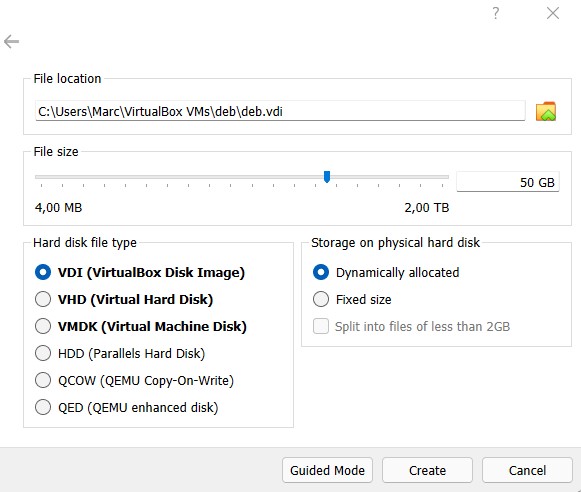
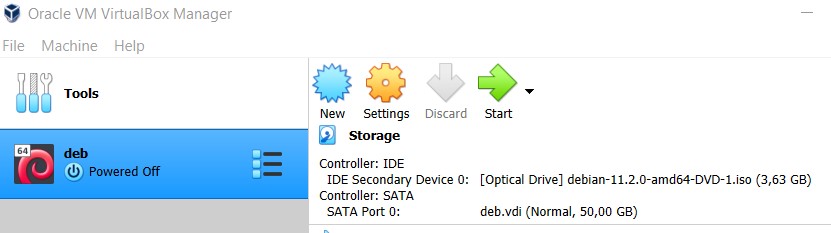
 To proceed further we will have to create a new user on the web-interface. Once that is done we are ready to go.
To proceed further we will have to create a new user on the web-interface. Once that is done we are ready to go.