Applied Cryptography: Foundations
In this segment we will have a look at the Chapter 1: Foundations, of the book Applied Cryptography: Protocols, Algorithms and Source Code in C, 20th Anniversary Edition by Bruce Schneier. We will focus mostly on the content that is relevant in terms of data security.
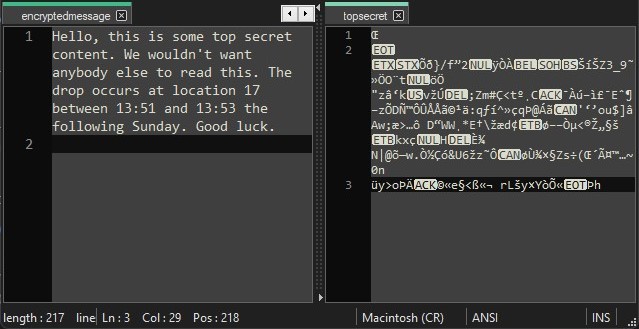
When send a secure message to a receiver we want to ensure that the message cannot be read by anyone except the intended receiver. Now if we just send the message in a plain text format, this will not really stop anybody from reading it if the message is intercepted. This is where encryption comes in, the process of disguising a message and hiding its content. The message can then turned back into its original state through decryption. The terms encrypt and encipher as well as decrypt and decipher are used interchangeably. A message that is encrypted is called a ciphertext. The term message doesn't really apply to just text, encryption can be applied to all kinds of data. This all falls under the umbrella of cryptography which is described by Mr. Schneier as the art and science of keeping messages secure.
Cryptography itself is also often responsible for authentication, integrity, and nonrepudiation.
- Authentication, from the greek word authentikos, meaning real, and genuine, refers to the fact that the receiver should be able to verify the messages origin.
- Integrity, from the latin word integritatem, meaning soundness, completeness, and wholeness refers to the fact that the receiver should be able to verify that the message has not been modified or substituted.
- Non-repudiation, from the latin word repudiare, meaning reject or putting away, refers to the fact that the sender should not be able to falsely deny that he ever sent the message.
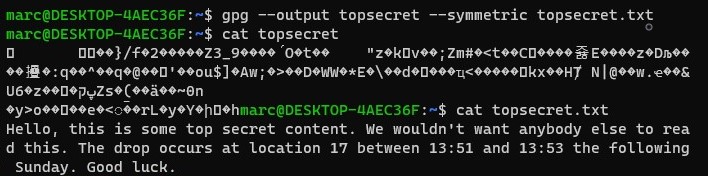
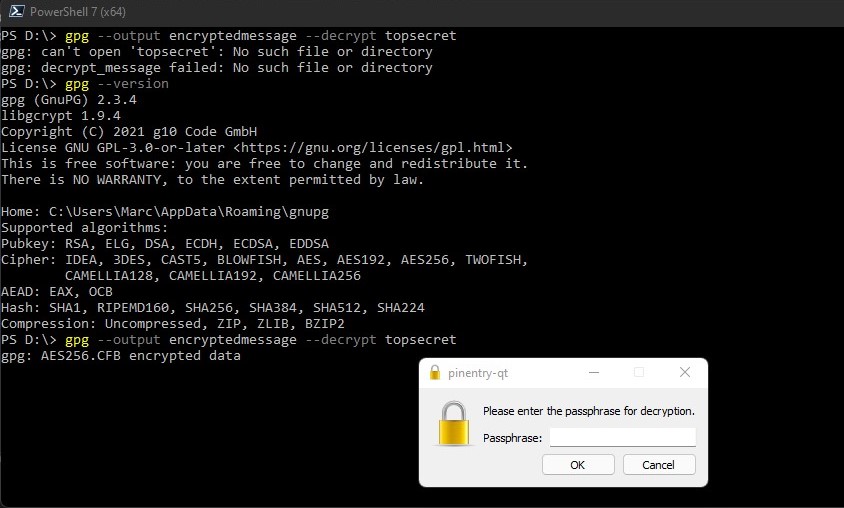
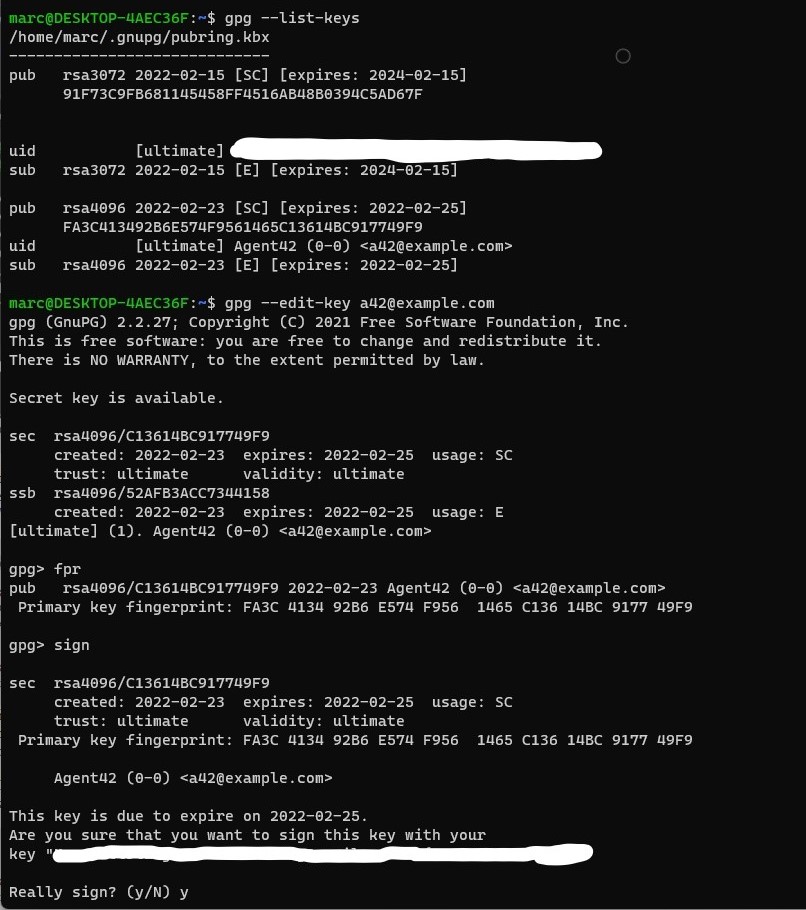
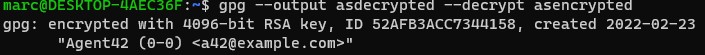
Then there is the topic of algorithms and keys. The cryptographic algorithm is also known as a cipher, it is the mathematical core function that is responsible to encrypt and decrypt the target data. Modern algorithms use one or multiple keys, which cause the encryption to be "unique" depending on said keys. There are multiple kinds of algorithms, one is the so called asymmetric algorithm type, where the key for encryption and decryption are different from each other. This is also known as a public-key algorithm. And there is symmetric encryption where description and encryption keys are interdependent. On the first glance it seems non-logical why anyone would use symmetric encryption since the one key concept is a lot more risky. The benefit of symmetric encryption is in the efficiency, especially when dealing with large amounts of data this can be rather significant. This does of course not prevent us from using a hybrid encryption, or in other words an asymmetric algorithm to share a key for a symmetric algorithm, and therefore bypassing the added risk in terms of security.
For a more detailed insight I highly recommend checking out the full chapter of the book.