The Art of Hacking
In this section we will have a closer look at Passive Reconnaissance and Active Reconnaissance from The Art of Hacking. Reconnaissance itself is an essential base which helps with the gathering of intelligence and mapping of a target environment. With it we can cut down on the time effort for an engagement significantly, especially in larger target systems.
Passive Reconnaissance (3.0 - 3.4)
Passive Reconnaissance (recon) is one of the most important elements when it comes to engagement. It refers to the research or reconnaissance that is done without directly engaging with the target itself (no scanning, phishing etc.), which would potentially make them aware that someone is actively looking for something.
Instead passive recon relies on things like researching publicly available information, etc. This can reveal extremely useful information which is commonly overlooked. As example you might find employee names, password dumps from previous breeches, test systems open to the internet, and a variety of other gems.
Skipping out on recon is will potentially cause you to overlook crucial information on the target system, such as vulnerabilities which might be of importance for any successful engagement. It is in general an invaluable source of intel that might provide you with information that you simply could not obtain in other ways without extensive effort.
In terms of methodologies we can utilize multiple techniques in the spirit of passive recon. For host and port discovery this can include things like:
- Search engines (including some techniques like Google dorking, etc.)
- Certificate Transparency (Find issued certificates)
- Guessing Hostnames (and check with nslookup if target exists)
- Regional Internet Registries
- Netcraft searches (to get some intel on the technologies used)
- Shodan.io and Censys.io searches (to see/search scan results of systems that are reachable online)
Another crucial source for recon are files that belong to a target. These can often be acquired through simple Web searches. With the right search parameter we can for example execute a targeted search for PDF, XLSX or password files. The Metadata in files can provide useful intel such as usernames, org info etc. Something like ExifTool can help with the extraction of such metadata.
Last but not least we shall not forget about the value of names, passwords, and other sensitive information that belong to a target organization. A valuable source of such information are public breaches (as example Adobe, Dropbox, etc.), some of which contain a significant amount of data that could be of interest, since many users reuse their passwords and usernames. Pastebin is another interesting source that can contain valuable information. Here we can also again use search engines for our advantage, by utilizing modified search queries to specifically search for sensitive information. Very useful for this specific purpose is the Google Hacking Database
Active Reconnaissance (4.0 - 4.3)
Active reconnaissance/recon differentiates itself from the passive form by the nature of active engagement with the target network. This could be port scanning, vulnerability scans, and other techniques which come at the risk of triggering some alarms or cause awareness on the targets side, assuming they monitor for such things.
In general active recon builds up on the passive recon and most often boils down to the following order of techniques:
- Port Scanning, to find additional an verify existing open ports
- Web Service review, to prioritize our targeting for an attack
- Vulnerability scanning
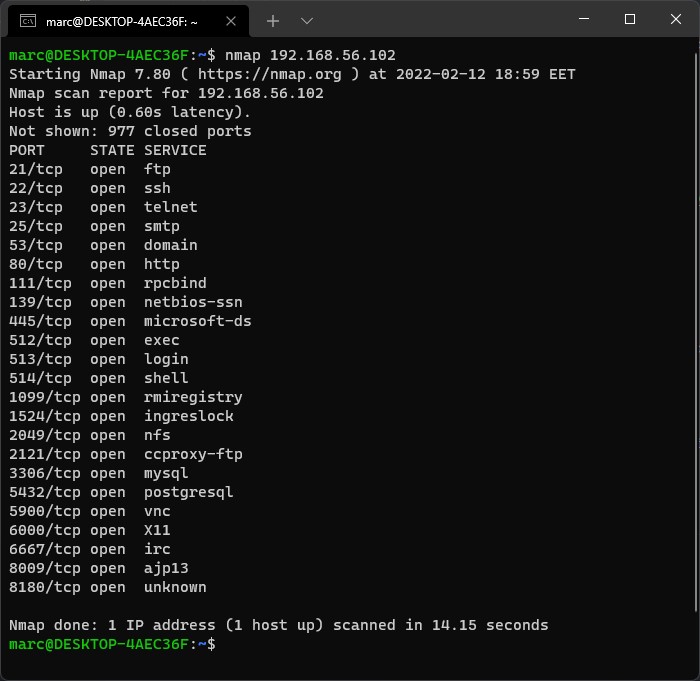
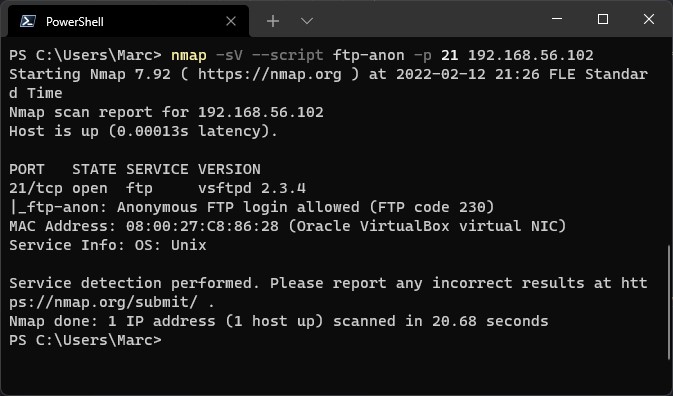
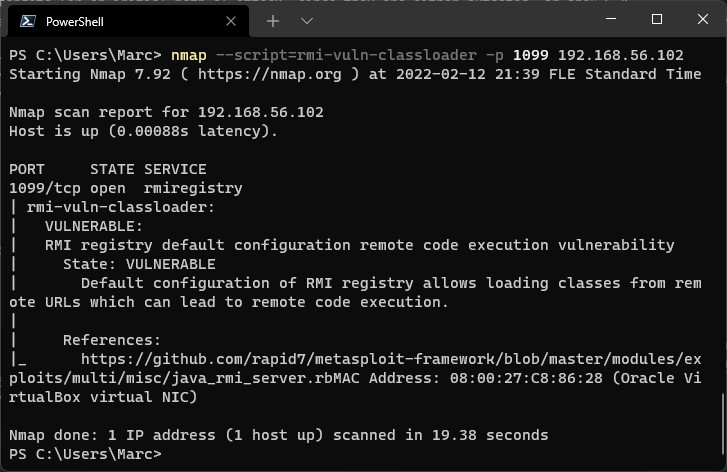
Port scanning can be done with a tool like Nmap, which is one of the most established and popular port scanners. The functionality is not simply limited to port scanning but also provides service detection, OS detection, and certain aspects of vulnerability scanning. There are also various other port scanning tools out there, such as Udpprotoscanner for UDP port scanning. For things like web service review there are tools such as EyeWitness, which can analyze a large amount of websites and providing a detailed report containing information about the header, screenshots, etc. to assist in the prioritization and identification of an ideal attack vector. This could as example be a web service page with an administrator login field.